
ComputerCop
The heavily distributed kid-monitoring software ComputerCop, which many police departments around the US gave to families for free, is doing far more harm than good, a new report by the Electronic Frontier Foundation alleges.
An eight-month investigation by the group — a nonprofit that focuses on civil liberties in the digital realm — says ComputerCop, which allows parents and guardians of children to monitor a child’s computer and Internet use, is sketchy in its effectiveness and falls short on protecting user data from spying. The EFF report also alleges that ComputerCop engages in shady business practices to convince law enforcement officials to spend taxpayer money on the software.
“Probably the biggest problem of all is that there are law enforcement agencies that aren’t actually paying attention to cybersecurity,” said Dave Maass, who wrote the EFF report. “Some of the biggest jurisdictions in the country are giving out software that makes kids less safe if they use it.”
ComputerCop’s chief executive, Stephen DelGiorno, stands behind his software.
“ComputerCop only shows parents what is on the computer at the present time,” he wrote to CNET in an email. “ComputerCop doesn’t block or filter children’s activities.”
Maricopa County Attorney’s Office public information officer Jerry Cobb said that it’s “ridiculous” to call ComputerCop “sypware.”
“This product is fundamentally no different than the parental controls that are available on countless digital devices and software used by kids today,” Cobb said. “In fact, most parents believe they have the right and responsibility to know what their children are doing online, and this product is a simple tool that allows them to do that.”
ComputerCop, which works on both Windows and Mac, has two primary features. One is a search feature that lets the user review videos and images downloaded to the computer, as well as search documents on the hard drive for “thousands of keywords related to drugs, sex, gangs and hate groups.” The second is a keylogger called KeyAlert. Keyloggers record all keystrokes made on a computer keyboard, including credit card information and username and password combinations.
However, Maass said that the keylogger in ComputerCop lacks basic protections and could put user data contained in those keystrokes at risk.
“Most devices do not have keyloggers,” he said. “If Maricopa County and ComputerCop are so confident in their software, then they can hire an independent information security team to evaluate the software and publish those results.”
EFF staffers Jeremy Gillula, a data and privacy expert whose research found that Android phones were leaking location history, and Bill Budington, a member of the Web Cryptography Working Group and a lead developer for the secure document-sharing software SecureDrop, evaluated ComputerCop for the advocacy group.
Broken search, leaky info
The EFF report deemed the search feature “unreliable” and explains that some computers returned a “giant haystack” of inaccurate information, while other computers returned better results from their built-in file-search function. An ancillary function of ComputerCop is to let parents see which websites their children have visited, but that’s only if the child is using the Internet Explorer browser on Windows or Safari on a Mac. While it’s true that a huge number of computers are sold with IE and Safari set as their primary browsers, it’s easy enough to download and use an alternative, like Chrome or Firefox.

EFF
The keylogger feature KeyAlert records keystrokes unencrypted on Windows computers, and on Macs they can be decrypted with the software’s default password. The software can also be configured so that trigger words email an alert to the computer’s owner.
KeyAlert must be installed separately from the rest of the ComputerCop software, but not all versions of ComputerCop have been distributed with it. There’s no way to configure KeyAlert for a particular user, so it’s possible to use it against anybody using the computer — not just kids.
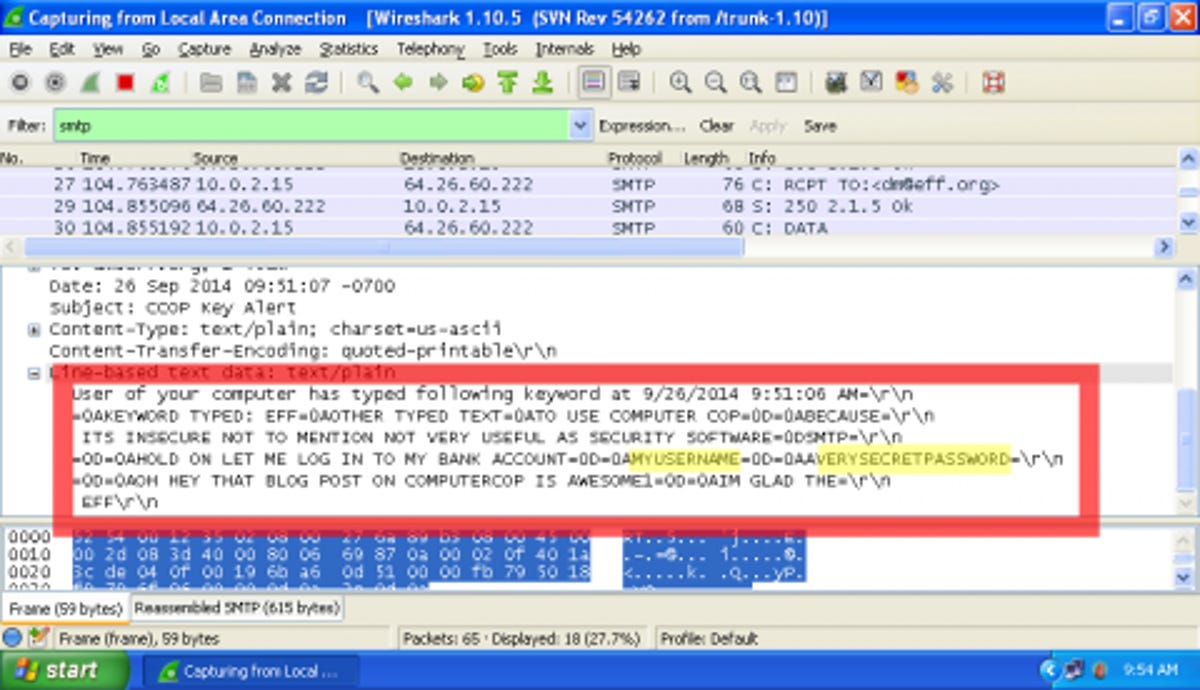
“When that happens, the software transmits the key logs, unencrypted, to a third-party server, which then sends the email,” the EFF report said.
If the logs are being emailed unencrypted, as alleged, then they could be read with relative ease, according to the report, which also included instructions for removing ComputerCop.
“There is no database collection or servers with stored information for third party spying,” said DelGiorno, refuting one of the EFF’s allegations. “The product’s keystroke utility is termed ‘limited’ because it captures only the keywords entered by the parent/guardian and small subset of words from the product’s keyword library such as ‘meet me.’ It does not capture every keystroke,” he said.
The EFF provided CNET with an email that they said came from ComputerCop’s keylogger email alert. The email included what appeared to be full text from a chat log, as well as the email header information indicating that the log was routed through two ComputerCop servers.
However, the Maricopa County Attorney’s Office website promoting their use of the software says that ComputerCop can, “Capture full text from online chat rooms, emails and instant messages,” as well as “Capture e-mails and text messages that contain specific keywords, phrases or addresses that you identify.”
New York’s Suffolk County, where the ComputerCop company is headquartered, has purchased more than 43,000 copies of the software since 2007, which appears to be the largest investment in the software, the report said. The report also said there appear to be close ties between the software company and the sheriff’s office there that involve ComputerCop’s parent company donating to the sheriff’s re-election campaigns, and the sheriff highlighting the software purchases in re-election campaign materials. The sheriff’s office did not respond to a request for comment.
Nell Hays, the public information officer for the Highlands County Sheriff’s Office in Florida, which was one of the largest law enforcement purchasers of ComputerCop, told CNET that Highlands County was unaware of the report’s allegations.
“I don’t believe there is a need for this product today that there was years ago,” she said, and added that her office now encourages more hands-on, in-person monitoring of children using the Internet. However, she still brings copies to public events to give away.
Highlands County Sheriff Susan Benton bought 10,000 copies of ComputerCop in 2008 with $42,500 of drug seizure money. That’s enough copies to give one to every family in Highlands County that has a child in school, the EFF said.
Hays said that of the 10,000 copies originally purchased, between 1,080 and 1,350 copies remained in the sheriff’s office. She said that the county had received “no complaints” about the software. The version of the software sold to Highlands County in 2008, ComputerCop Deluxe, included the keylogger feature.
San Diego District Attorney Bonnie Dumanis bought 5,000 copies of ComputerCop in 2012 using $25,000 of asset forfeiture money the county had collected.
Steve Walker, a spokesman for Dumanis, said that because of the EFF report the office has “issued an alert to everybody who has the software.”
Dumanis’ warning cautions people to avoid activating the keylogger feature, and it advises people who have the software already installed on how to deactivate the keylogger because of “potential privacy issues with the software.”
However, Walker told CNET, “we still recommend people use it, with the warning.”
ComputerCop also engaged in questionable business practices, the report said. The company claimed an endorsement from the US Treasury Department’s Executive Office for Asset Forfeiture. ComputerCop’s DelGiorno admitted to the EFF that he had altered a letter from the Treasury Department, which led to the department issuing a fraud alert for ComputerCop.
The company also touted an endorsement from the American Civil Liberties Union, which the ACLU apparently never made. The National Center for Missing and Exploited Children endorsed ComputerCop for only one year, from 1998 to 1999, but ComputerCop still claims an endorsement from the center.
Maricopa County email to CNET about ComputerCop
Correction, October 6 at 7:02 p.m. PT: Clarifies that Jeremy Gillula and Bill Budington are EFF staffers.
Update, October 3 at 5:15 p.m. PT: Adds statement from Arizona’s Maricopa County Attorney’s Office and response from the EFF.
Update, October 2 at 6 p.m. PT: Adds statement from ComputerCop and information that the Highlands County distribution of the program included the keylogging feature.




