
Seth Rosenblatt/CNET
It might seem like security roulette to test the Blackphone at a conference full of hackers, but what better place to gauge the Android-based smartphone’s claims of being extra safe?
After three days of toting the device everywhere at DefCon in Las Vegas in August, here’s what I concluded: the security- and privacy-focused phone definitely makes mobile security and privacy features easier to use.
But that doesn’t mean this superphone is supersecure.
Built by SGP Technologies, a Switzerland-based joint venture of security company Silent Circle and hardware manufacturer Geeksphone, the Blackphone claims to be more secure and private than standard phones built around Google’s Android mobile operating system software. The reason, say its creators, is because it has a customized version of Android geared toward privacy and comes pre-installed with nine security apps.
Phil Zimmermann, the founder of Silent Circle and a veteran of the 1990s “crypto wars” that saw tech companies and industry advocates force the US government to repeal laws that deemed cryptography a weapon, told CNET in August that encryption — technology that protects your digital communications from eavesdroppers — is essential to ensuring privacy.
Tougher security bolsters the Blackphone (pictures)






“In the ’90s, if you used strong crypto, you had to explain yourself. Today, if you’re not using strong crypto, you have to explain yourself,” Zimmermann said.
The Blackphone retails for $629 in the US (it’s also available internationally), and it currently comes with a free service contract bundle for its nine pre-installed security and privacy apps worth an additional $879. However, that’s a promotional deal that ends September 30.
Blackphone didn’t respond to a request to explain how the services will be offered from October 1. However, if you have to pay for them in full, it becomes much harder to recommend the Blackphone since you can just install most of them on your current phone without being tied to the Blackphone hardware.
The Blackphone is trying to capitalize on the fear of government surveillance and compliant phone service providers, topics which have stayed front page news since Edward Snowden leaked spying documents to the press last summer. But despite the surge of public interest, the Blackphone faces a difficult road ahead.
Today, consumers are faced with a multitude of smartphone choices. A crowded field of hardware manufacturers led by Samsung and including Motorola, LG, Sony and HTC have partnered with Google’s Android to take on Apple and its iPhone. Apple and Samsung, however, lead the smartphone pack by a long shot. Further down the line, there are Windows Phones and Blackberry devices, and even Mozilla and Ubuntu are making phones with open-source operating systems.
Point being, there’s a lot of competition in the phone market. What will give the Blackphone longevity is its appeal to people who place a high value on privacy — if they flock to it.
Related stories:
- Blackphone takes you off the grid for $629 (hands-on)
- New Blackphone aims to quash surveillance threat
- Google to encrypt data on new version of Android by default
- Cryptographer creates Blackphone to “ensure privacy”
- GeeksPhone Blackphone keeps your calls and data off the grid (video)
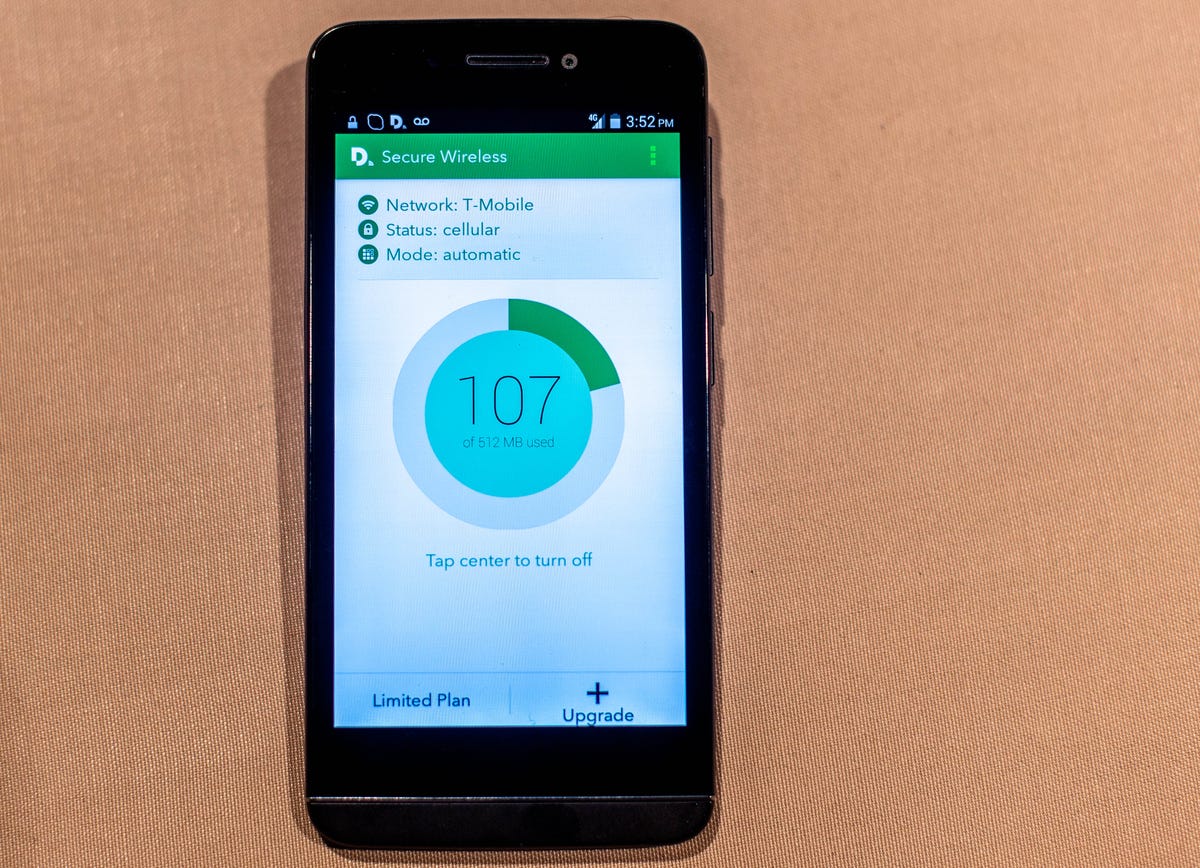
The included apps and services offer an excellent deal — if you get them before September 30. It comes with two years of Silent Circle Mobile’s end-to-end encryption for text messages and phone calls; three one-year friends-and-family Silent Circle subscriptions so you have some friends to have encrypted conversations with; two years of Disconnect’s Secure Wireless VPN at 1GB per month; and two years of SpiderOak cloud storage at 5GB per month.
There’s also the free Smarter Wi-Fi Manager from Kismet, which performs advanced Wi-Fi protective functions by preventing you from accidentally connecting to free public Wi-Fi networks, learning your preferred Wi-Fi locations and disabling Bluetooth as necessary.
After the two-year limit, the paid services each will cost around $10 per month.
If you want to shield voice conversations and text chats from prying eyes in real time, protect photos and videos stored on the phone and in the cloud, and ensure those connections are protected against hacking, the Blackphone should be on your short list of new phones to try out.
The Blackphone device itself has all the bells and whistles of a standard mid-tier smartphone. It comes with 16GB of storage, and runs on a 2GHz Tegra 4i quad-core processor. The 4.7-inch, 1,280×720-pixel touchscreen is a high-definition, capacitive multitouch display. The Blackphone also comes with an 8-megapixel rear camera, a 5-megapixel front camera, 802.11n Wi-Fi, GPS and Bluetooth 4.0.
Blackphone’s leadership know they’re in for a challenge. Dan Ford, Blackphone’s chief security officer, said that it’ll take “three to five years” to prove the Blackphone.
“We know what we’re doing is a niche market. We’d like to take 1 to 2 percent of the market,” Ford said. Seeing as how billions of new Internet users are expected to go online for the first time because of smartphones in the next few years, a single-digit percentage niche could still make for a sustainable business.
Blackphone, meet the world
I didn’t test the Blackphone by trying to hack into it, but I did use its security tools to protect me when using both Wi-Fi and mobile data on the phone.


Seth Rosenblatt/CNET
One task I set was to safely use the notoriously risky public Wi-Fi network at DefCon. I fired up the Secure Wireless virtual private network (VPN) app from Disconnect on the phone and started browsing the Web. The VPN app kept my credentials such as my password and IP address from being displayed on the conference’s Wall of Sheep — a scrolling list, projected on a wall, of log-in credentials from attendees who don’t take safety precautions. It’s not foolproof, but an adversary that’s attempting to steal your credentials will have to work much harder to get them.
According to Jon Callas, Silent Circle co-founder and chief technology officer, the Blackphone owes some of its inspiration to the hacker-customized, Android-based Ninja Phone created by the Ninja Hacker Group and released at DefCon in 2012. While the Ninja Phone was built to show the possibilities of being part of a private mobile phone network, the Blackphone is designed for people on popular GSM carrier networks (like AT&T and T-Mobile) around the world.
The Blackphone’s cryptographic tools are based on a unique flavor of Android. It runs PrivatOS, a customized version of the Android Open Source Project (AOSP), which is Android before Google adds its services like the Google Play store, Gmail and Google Maps. AOSP is what other Android device makers besides Google, such as Amazon and China’s Xiaomi, use to run their devices.
PrivatOS is based on Android 4.4 KitKat, the latest version of Google’s mobile operating system, and Blackphone’s makers expect to update it to Android L, the next major version of Android, when Google releases it before year’s end.
In fact, one of Blackphone’s selling points is that it will update frequently — something that many other Android makers don’t do. leading to Android’s notorious fragmentation problem. Blackphone promises the phone will receive over-the-air updates of PrivatOS for at least two years, and already has shipped four updates — including one on August 7, just before DefCon kicked off in Las Vegas.
That led to some hand-wringing at the show since Blackphone was selling phones there, nobody wants to install an over-the-air phone update at a hacker conference — the risks of getting hacked are too great.
Not a hack-proof phone
DefCon saw a controversial hack successfully gain root access on the Blackphone, a procedure which opened deep, system-level controls to the hacker.

Seth Rosenblatt/CNET
Jon Sawyer, known as @TeamAndIRC on Twitter and the chief technology officer of the security firm Applied Cybersecurity, disclosed three Blackphone vulnerabilities at the show.
Although there was some friction between Sawyer and Blackphone initially, Blackphone addressed the hacks in a blog post and a follow-up. While it’s a truism in the security world that everything is hackable, Sawyer’s take was that the vulnerabilities that he exploited shouldn’t have existed in the first place.
Sawyer told CNET that the basic security tests required of manufacturers by Google before installing the Google Play store and other Google apps would’ve caught the most severe of the vulnerabilities.
“No device should have shipped with something like this, I’ve only seen it on non-Google approved devices like the original Amazon Kindle Fire and the Blackphone,” he said, even though the vulnerability was fixed the day before DefCon began.
Nevertheless, the Blackphone team earned some respect from security researchers for rapidly patching the vulnerabilities and notifying the public.
Better but still flawed on-the-go security
Critics rightfully point out that the Linux-based Android is not a secure operating system by default. But for phone makers, there’s little choice beyond Android. Apple’s iOS mobile operating system only runs on Apple’s hardware, the iPhone and iPad tablet, and other mobile operating systems just don’t have the same traction with consumers that Android does.

Seth Rosenblatt/CNET
There are other benefits to using the Blackphone, such as better stability for Silent Circle’s apps. Zimmermann said that the Silent Circle secure apps do not “float” on top of PrivatOS, but are instead baked into the system.
This improves their stability to the point where they can be used as the default phone and text messaging apps, which is important because few people will use an encrypted app if its appears to be of lower quality than one that’s unencrypted. To Zimmermann, you’re not just paying for privacy, but for a level of quality identical to an unencrypted phone.
“To us, our whole business model is that we charge money for our services. If you’re not paying for the product, then you are the product,” he said, reiterating the trade-off that many Silicon Valley giants like Google and Facebook have staked their empires on.
Phone calls I made with Silent Phone, the Silent Circle phone app, sounded the same whether encryption was turned on or off. The encryption itself was easy to toggle on a per-call basis, adding only one extra step to verify that a call was encrypted.
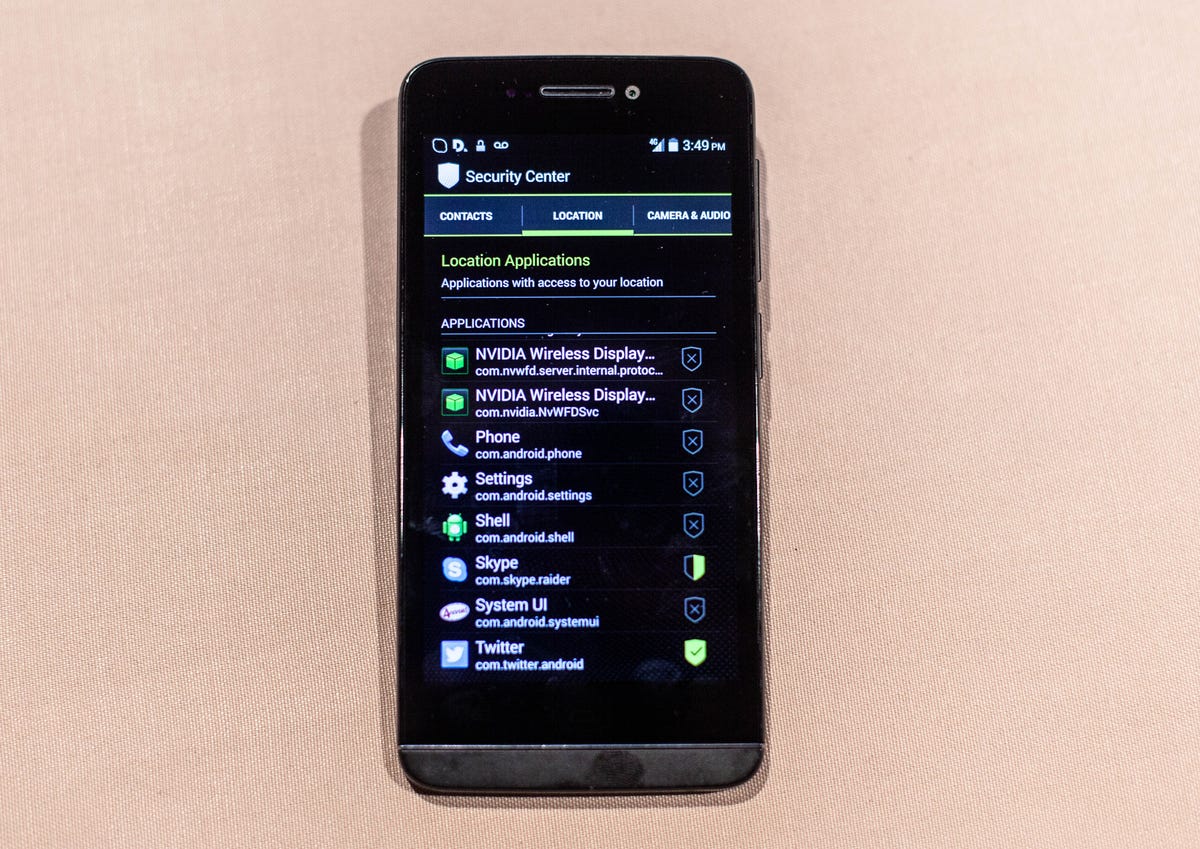
The phone also lets you toggle app permissions at will, so that if Facebook’s asking for access to your contact list and you don’t want to give it, you don’t have to.
In theory, this is a great feature, and one that Google appears to be working on. In practice, the Blackphone’s implementation was erratic. After revoking Facebook’s permission to use the camera and rebooting, I was still able to take a photo through Facebook and save it to the phone. But after a second reboot, the revocation stuck and blocked Facebook from using the camera.
The Blackphone also lacks a dedicated Pretty Good Privacy (PGP) encryption tool for email. This may seem strange given that Zimmermann created PGP in the 1990s and is a driving force behind the Blackphone. There are several PGP managers and email clients for Android that you can install on your own. But why doesn’t it come with one?
Ford said that because of the legal problems that Edward Snowden’s suspected email provider Lavabit encountered last year, he didn’t want to highlight any one service.
“Based on the issues that Lavabit had, we do not want to be in a position as being seen as endorsing any particular client,” Ford said, but then appeared to contradict himself. “However, we have been approached by some email clients and are currently reviewing [them.]”
Another potential problem for Blackphone users is that it doesn’t ship with an app store, so you have to download one yourself. Blackphone recommends the Amazon App Store, which means you need to go to the Blackphone’s Settings and enable installing apps from Unknown Sources. While this is an extra step you don’t have to do on other Android phones because they come with the Google Play store, this will only take you a few minutes.
The problem is that enabling Unknown Sources weakens the phone’s security and could allow unauthorized apps to be installed. The way that Android is built, you’re forced to choose between the potential risk of Unknown Sources or allowing Google’s services on your phone. There’s no way around it.
While the Amazon App Store is large, like Google it adds trackers to the apps it sells. Think again if you’re trying to get away from tracking by going to Amazon.
You could go with an open-source app store such as F-Droid, but that leaves you with a smaller selection. You could, in theory, disable Unknown Sources each time after installing a new app, but that’s a colossal pain in the butt.


Seth Rosenblatt/CNET
Bottom line is that when it comes to apps on the Blackphone, you have to trade some of your data for the better service of a larger store — the very thing that Zimmermann is railing against — and run a less secure phone at the same time.
Why use a phone that can be hacked?
Between TeamAndIRC’s hacks, flaws in the Android operating system, and Blackphone’s own struggles to make Android more secure, the Blackphone is not only vulnerable to harm, it may not even be the most security-hardened phone out there.
So why use it?
One reason is that there’s no such thing as an unhackable phone. Apple’s iOS and iPhones have been hacked, as have Androids, Windows Phones and others.
Zimmermann suggests another reason: society is changing.
“Phone companies have had 100 years of culture where they’ve been cooperative with governments to infringe on the privacy of their customers,” Zimmermann said.
“What we’re starting to see now is that they want to protect [their customers’] privacy,” he said, a bold claim given that there’s only one phone company, Dutch carrier KPN, that supports the phone directly. Since the phone is unlocked, you can take it to any GSM carrier, but Zimmermann emphasized carrier support as being essential to the phone’s success.
He compared it to the 18th-century myth that tomatoes were poisonous.
“KPN is breaking ranks by eating tomatoes in public. They can offer their customers privacy with our help,” he said, calling it “a hugely significant turning point.”
Blackphone may have the measure of the privacy-concerned general public right, but how big of a turning point the phone will prove to be depends on consumers and carriers, two groups whose interests are not always aligned, to put it mildly.
Still, the most remarkable thing about the Blackphone is that it makes encrypted communication as easy as sending a text message. If regular smartphone makers made encryption this easy, privacy would be the new normal.




